Internet of Things Security: Challenges and Solutions

Credit: Wilgengebroed on Flickr, CC BY 2.0, via Wikimedia Commons
Author: Dr. Qiang Lin
Considered the first Internet of Things (IoT) device, the toaster John Romkey created could be turned on and off over the Internet during the October ’89 INTEROP conference! Since then, more people have begun to use IoT devices. Simply put, IoT connects devices with the Internet, from things as simple as smart light bulbs and coffee makers to things as complicated as robots and drones.
Billions of connected devices (e.g., Amazon Alexa and Tesla cars) deliver new experiences to people throughout the world. Unfortunately, as embedded, obscured, interdependent and continual introduction of IoT products and services proceeds, we have lost some ability to know where these technologies reside, or how they impact us. In addition, this growth brings increased security risks – hackers quickly target this rich, but vulnerable, landscape. A Distributed Denial-of-Service (DDoS) attack, occurring on October 21, 2016, brought down Twitter, Netflix, and CNN. It was orchestrated using a Mirai botnet, composed of 100,000 “malicious” IoT devices like digital cameras and video recorders with an extraordinary attack strength of 1.2 Tbps.
In other words, IoT is ubiquitous, but not mature enough to be entirely safe. We face many IoT security threats today, such as these:
- Lack of compliance: New IoT devices come out almost daily, many with undiscovered vulnerabilities, because manufacturers do not spend enough effort on security.
- Lack of user awareness: Instead of targeting devices directly, hackers target humans through social engineering attacks using IoT devices.
- Untimely device updates: Updates are critical for maintaining security – the updates should be done as soon as vulnerabilities appear. However, some IoT devices continue operating without the necessary updates.
- Lack of hardening: Many IoT devices operate autonomously without user intervention, but they should be physically secured so as to be tamper resistant.
- Botnet attacks: A single device infected with malware poses little threat, but a collection of them can topple anything.
- Industrial espionage: Spying and intruding through IoT devices are serious, as sensitive data may be compromised.
- Hijacking: 7 million ransomware attacks were reported in third quarter of 2020!
- Data integrity risks in healthcare: If hackers gain access to medical equipment, the controlled devices can send false signals, making healthcare practitioners take inappropriate actions as they care for patients.
- Rogue devices: As Bring Your Own Device (BYOD) practices become more prevalent in enterprise and in-home networks, rogue, even malicious, devices are introduced, collecting or altering sensitive information.
To counter various IoT security threats and risks, I propose a four-layered IoT security architecture to achieve the defense-in-depth effect, as shown in Figure 1.
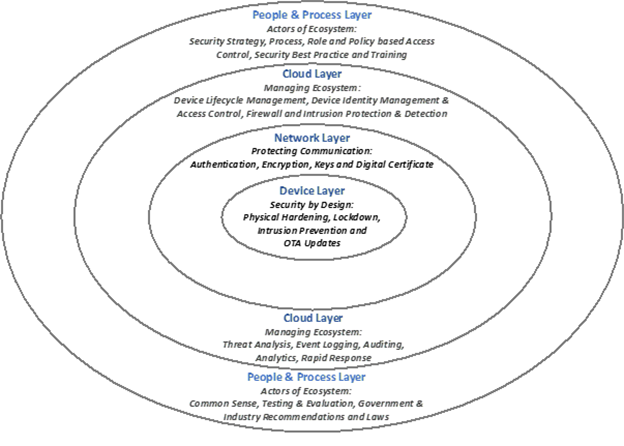
Figure 1 – A Four-Layered IoT Security Architecture
IoT devices must have security by design, or intrinsic security, instead of add-on security or extrinsic security because most IoT devices are “closed.” In other words, customers cannot add security software themselves. Were someone to try, such tampering would likely void the warranty. Additionally, IoT devices must be protected continuously after the software begins running. Host-based protections will help, including physical hardening, lockdown, and network-facing intrusion prevention.
Unfortunately, vulnerabilities will eventually emerge while devices are in operation, at which point the devices will need to be patched. However, nobody wants to visit each device for updates. Therefore, Over the Air (OTA) updates through wireless communication (i.e., making it possible for companies to roll out new patches without having to recall those devices) should be built into IoT devices before they are deployed.
Network Layer
This layer protects communication among IoT devices and the cloud, including:
- Symmetric or secret key encryption: Both the sender and receiver use the same secret key for encryption and decryption. Symmetric encryption requires fewer computing resources and runs fast. However, distributing the encryption key is still a major issue.
- Asymmetric or public key encryption: Each IoT device gets a pair set of one public key and one private key, for the encryption process. The public key is made known to the “public” (i.e., any other devices and the cloud), but the private key is only held by the owner device. The sender will use the receiver’s public key to encrypt the message, then send the encrypted message to the receiver. The receiver will use its private key to decrypt the encrypted message. Asymmetric encryption avoids the key distribution issue but requires more computing resources and takes longer to encrypt and decrypt.
- Authentication: Identities of IoT devices can be authenticated using traditional passwords, but public key authentication is the next step in improving IoT security because many IoT devices operate without human intervention. Public key authentication requires that each device first get a public key and private key set, and then get its digital certificate (with its public key coded in it) from a Certificate Authority (CA) so that the digital certificate can be used later to certify the ownership of a public key by the named IoT device of the certificate.
- Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocol installs publicly trusted TLS or SSL certificates for authentication and encryption.
Cloud Layer
The cloud layer is the keeper of the IoT ecosystem, responsible for the lifecycle management of IoT devices, including their:
- Public and private key pair generation, enrollment, distribution, management, and revocation through a Public Key Infrastructure (PKI)
- Identity management and access control
Since most IoT devices will communicate with the cloud, including for data exchange, traditional endpoint security measures, such as antivirus, firewalls, and intrusion prevention and detection are important to protect the cloud. Additionally, three more measures are necessary:
- Installing an IoT security analytics capability (e.g., to collect, aggregate, monitor, and normalize the data from IoT devices) in the cloud to alert security engineers about any anomalies (e.g., suspicious or even malicious events).
- Monitoring IoT devices (e.g., medical equipment used in hospitals) using analytics as an interim solution when upgrading them would take years.
- Identifying high-priority targets in the IoT ecosystem and paying special attention to them (e.g., network gateways), given that an attack could be transmitted across an entire network if not caught early.
People and Process Layer
This layer defines what people and processes can do for IoT security, including:
- Creating the IoT security strategy, processes, and policies for enterprises to follow.
- Implementing role-based and policy-based IoT ecosystem access control to avoid accidental human errors and malicious attacks.
- Following best practices, such as Norton’s Tips to secure IoT devices.
- Training people who access and use IoT devices so that they become aware of and responsible for IoT security – knowing what to watch for, do, and avoid in case of IoT security incidents.
- Performing different testing and evaluations throughout the IoT ecosystem and lifecycle, such as device, cloud, and mobile application testing, integration testing, network penetration testing, and even reverse engineering of certain devices.
- Referencing an industry IoT device security rating before buying new devices and following government IoT security recommendations when available.
- Being aware of IoT security-focused laws, including two laws from the U.S. – California SB-327, passed in 2018, and Oregon House Bill 2395, passed in 2019, as well as UK Code of Practice, published in 2018.
IoT security has become an increasingly critical piece of overall cybersecurity for Federal agencies and enterprises. MITRE has been at the forefront of cybersecurity research and a trusted advisor to Federal agencies and enterprises. In particular, MITRE has established a globally accessible knowledge base, MITRE ATT&CK®, which presents adversary tactics and techniques based on real-world observations. One area of ATT&CK is Internet Accessible Device, which corresponds to IoT security. Meanwhile, MITRE is also building Cyber Analytics Repository (CAR), a knowledge base of analytics based on ATT&CK.
As more sensors are embedded in the advanced systems, such as the F-35’s sensor fusion system, patient monitoring solutions, and smart cities, and, as more things become interconnected, it is becoming more urgent to bolster IoT security for reasons of national security and to enable a safer life for us as individuals.
Qiang Lin is an Information Systems Engineer at MITRE and Adjunct Faculty in the Department of Electrical and Computer Engineering at George Mason University. He worked at Deloitte and SAIC previously and has a PhD in Computer Engineering from West Virginia University.
© 2020 The MITRE Corporation. All rights reserved. Approved for public release. Distribution unlimited. Case number 20-3577
MITRE’s mission-driven teams are dedicated to solving problems for a safer world. Through our public-private partnerships and federally funded R&D centers, we work across government and in partnership with industry to tackle challenges to the safety, stability, and well-being of our nation. Learn more about MITRE.
See also:
5G: How it Works and What it Brings
The Person at the Other End of the Data
A Social Scientist Examines the Role of Technology in our Lives
Building Smarter Machines by Getting Smarter About the Brain
Marcie Zaharee and MITRE’s Open Innovation Challenge
Another Update on the Aviation Industry with Michael Wells and Bob Brents
Interview with Dan Ward, Debra Zides, and Lorna Tedder on streamlining acquisitions
Consequences and Tradeoffs—Dependability in Artificial Intelligence and Autonomy
fleetForecaster Keeps U.S. Aviation System a Step Ahead
